Imagine your phone rings. It’s your bank manager. You recognize their voice perfectly. They sound panicked.
“There’s been a security breach on your account,” they say, “We’ve locked it, but we need to verify your identity to secure your funds. I’m sending you a link to a secure portal. Please log in immediately and confirm your social security number and password so we can move your money to a safe holding account.”
You’re smart. You know about phishing. But this isn’t an email with bad grammar. This is a voice you know. The link they send looks legitimate. The website is a perfect copy of your bank’s portal. The urgency is overwhelming.
This is not a hypothetical scenario. This is an AI-powered deepfake scam, and it’s happening right now. Generative AI has given criminals the power to clone voices with just a 15-second audio sample and create hyper-realistic fake videos.
The old security methods—a password, a firewall—are useless against this. The “castle-and-moat” security model is dead.
So, how are banks, the institutions that hold our entire financial lives, supposed to fight an enemy that can perfectly impersonate anyone?
The answer is a radical shift in thinking. It’s a philosophy that begins with a simple, powerful, and slightly paranoid premise: “Never Trust, Always Verify.”
This is the what is a “Zero Trust” security model explained. This is your advanced guide to how banks are fighting deepfakes, why your login experience is changing, and what this new security frontier means for you.
(Disclaimer: This article is for educational purposes only. It is not financial or security advice. We are not cybersecurity professionals, but we are synthesizing expert information to help you understand these complex topics. Always consult with a qualified cybersecurity expert and your financial institution for professional advice. Protecting your assets is your responsibility.)
The New Enemy: What Are AI Scams and Deepfakes?
To understand the solution, we must first face the terrifying reality of the problem. Generative AI security risks have changed the game. Scammers no longer have to trick you; they can impersonate trusted sources with terrifying accuracy.
What is a Deepfake Scam Explained Simply?
A “deepfake” is a portmanteau of “deep learning” (a type of AI) and “fake.” It is a synthetic video or audio recording that is algorithmically created to look and sound just like a real person.
- Deepfake Voice Scams: Also known as AI voice cloning scams, these are the most common. An attacker finds a clip of a person’s voice—from a podcast, an Instagram video, or even a voicemail. They feed this into an AI model, which can then generate new audio of that person saying anything the scammer types. This is the “panicked bank manager” or “family emergency scam” where a loved one calls you asking for money.
- Deepfake Video Scams: These are what you see on social media, where a celebrity appears to be endorsing a new, fraudulent crypto investment. They can also be used in live video calls. Imagine a scammer getting on a Zoom call with a company’s finance department, appearing to be the CEO and ordering an urgent wire transfer. This is an advanced form of business email compromise (BEC) with AI.
How Generative AI Creates Convincing Fakes Beyond Video and Voice
The threat isn’t just audio and video. AI-powered phishing attacks are now hyper-personalized. An AI can scan your social media, find your boss’s name, learn the project you’re working on, and craft a perfectly worded, context-aware email that is 100% indistinguishable from a real one. It will have no typos, use the correct corporate jargon, and reference real-life details.
This leads to a new, dangerous form of fraud: synthetic identity fraud prevention is now a top priority for banks. This is where a scammer uses AI to combine real and fake information—a real social security number with a fake name and a generated address—to create a “synthetic” new person. This new “person” then applies for loans and credit cards, builds up a credit history, and then “busts out,” taking all the money and disappearing, leaving the bank with no real person to chase.
The Old Way Is Broken: Why Traditional Security Fails
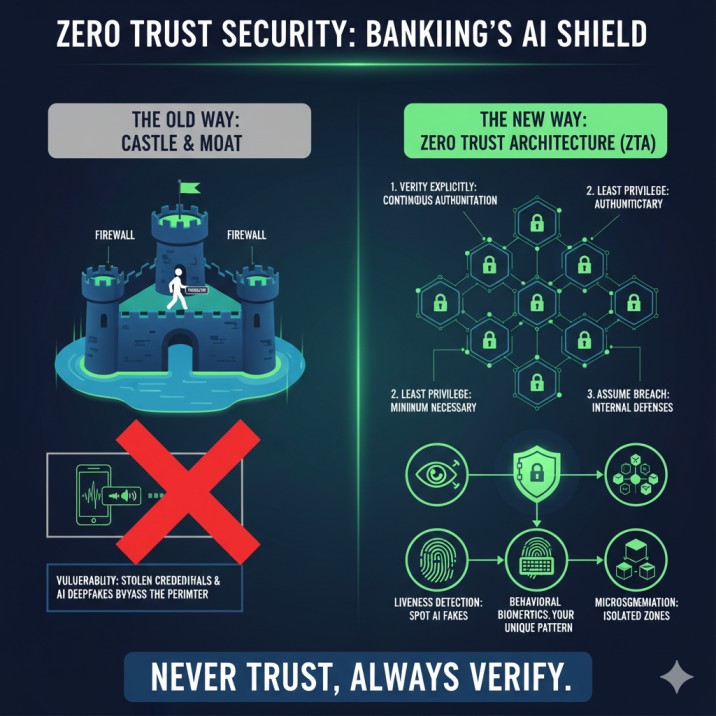
For decades, we secured our data like a medieval castle. This is the traditional “castle-and-moat” security model.
What is the “Castle-and-Moat” Security Model?
Think of a bank branch. It has thick walls (the firewall), a big moat (the internet), and one single, heavily guarded drawbridge (the VPN or login page). The goal is to keep “bad guys” out.
But what happens once a bad guy gets in?
Once you’re past the drawbridge, you are “trusted.” You can walk around the castle, access the files, and look around. This model has a fatal flaw: it trusts too much.
How Stolen Credentials Defeat Traditional Security
In a castle-and-moat model, the only thing that matters is the “secret password” (your login credentials). But what happens when those credentials are stolen?
- A scammer uses an AI-phishing email to get an employee’s password.
- They log in.
- The system says, “Welcome, trusted user! Go right ahead.”
The scammer is now inside the castle, free to steal data, initiate fraudulent transfers, and set up backdoors. This is why firewalls and VPNs are no longer enough. A VPN (Virtual Private Network) is just a “secret tunnel” into the castle. Once the attacker steals the key to the tunnel, it’s useless.
The perimeter is gone. Your bank’s data is in the cloud. Employees work from home. Customers log in from coffee shops. There is no castle. There is no moat.
The Ultimate Defense: What is a “Zero Trust” Security Model?
If you can’t trust anyone outside the network, and you can’t trust anyone inside the network, what’s left? You trust no one.
This is the birth of the Zero Trust architecture (ZTA).
The Core Philosophy of Zero Trust: “Never Trust, Always Verify”
Zero Trust is not a product, a piece of software, or a device. It is a completely different philosophy and a strategic approach to security.
It assumes that the network is already compromised. It assumes an attacker is already inside. It assumes the person logging in is an imposter until proven otherwise.
In a Zero Trust world, there is no “inside” or “outside.” There is only “unverified” and “verified.” And that verification is continuous.
The 3 Core Principles of Zero Trust Security Explained
To understand how does Zero Trust work, you need to know its three pillars, as defined by authorities like the National Institute of Standards and Technology (NIST) in their SP 800-207 guidance.
- Verify Explicitly:This means every attempt to access any resource must be authenticated and authorized. It’s not enough to just log in once. You want to access a file? Prove who you are. You want to open an application? Prove it again. You want to send a transfer? Prove it a third time. This continuous verification security model checks who you are, what device you’re on, where you’re located, and what you’re trying to do, every single time.
- Use Least Privilege Access (LPA):This is one of the most important principles of Zero Trust. What is least privilege access explained simply? It means you only get access to the bare minimum you need to do your job, and only for the time you need it.
- Old Way: A bank teller logs in and can see all customer accounts in their branch.
- Zero Trust Way: A bank teller logs in. They can’t see anything. When a customer walks up, the teller requests access to that specific customer’s account. The system grants it for 10 minutes. After 10 minutes, the access is automatically revoked.If a scammer steals that teller’s password, they can’t steal the whole database. They can only see what the teller could see: nothing.
- Assume Breach:This is the mindset. You must assume the attacker is already in your system. This forces you to build defenses inside the network, not just on the edge. How do you stop an attacker from moving around?
How Does Zero Trust Architecture (ZTA) Actually Work?
This is where the “Assume Breach” principle gets technical.
What is Microsegmentation in Zero Trust?
If your bank’s network is a castle, microsegmentation is like filling the inside of the castle with solid rock and carving out tiny, sealed rooms for every single person and application.
Instead of one big “trusted” network, microsegmentation in Zero Trust breaks the network into thousands of tiny, isolated zones. A “segment” might be a single application, a single server, or even a single user.
Each tiny room has its own locked door. To move from the “email server” room to the “customer database” room, you have to pass through another security checkpoint.
How this stops an attacker: A scammer phishing an employee’s password might get them into the “email” room. But when they try to move to the “wire transfer” room, the system stops them. It says, “We know who you are, but the email server is never allowed to talk to the wire transfer system.” The attacker is trapped and can be easily identified.
The Critical Role of Identity Management (IAM) in Zero Trust
Zero Trust is obsessed with one question: Are you really who you say you are?
This is why Zero Trust identity management, or IAM, is the heart of the whole system. Your password is no longer your identity. Your identity is a combination of many factors:
- Something you know: Your password.
- Something you have: Your phone (for a push notification or code).
- Something you are: Your fingerprint or your face.
This is multi-factor authentication (MFA) for online banking, and it is the absolute baseline. But Zero Trust goes further, checking your context. Is your device secure? Is it patched? Are you logging in from a new country at 3:00 AM? All of this builds a “trust score” for your identity in real-time.
Zero Trust in Action: How Banks Are Fighting Deepfakes and AI Scams
This philosophy is perfect for the financial industry cybersecurity trends of today. Banks are actively implementing Zero Trust in financial services to build a fortress against AI-powered fraud.
Here’s how they are connecting these abstract principles to the real-world threat of deepfakes.
Using Advanced Authentication to Defeat Deepfakes
If a scammer can deepfake your face and voice, how does a bank know it’s you?
How Banks Are Using “Liveness Detection” to Spot Deepfakes
When you use your banking app and it asks you to take a video selfie to verify yourself, it’s not just matching your face. It’s performing a “liveness check.”
This is advanced fraud analytics for finance. The app will ask you to do something an AI can’t do easily or in real-time.
- “Please turn your head slowly to the left.”
- “Please blink three times.”
- “Please read these random numbers out loud.”
A static deepfake photo can’t do this. Even a video deepfake will struggle to respond to a random command in real-time with the correct lighting, reflections, and fluid motion. This is a core part of how banks verify identity in a Zero Trust world.
The Rise of Biometric Authentication in Banking
Biometric authentication in banking is your “something you are” factor. But even this is being challenged by AI. What’s the next step?
What is Behavioral Biometrics? The New Frontier
This is the most advanced and “invisible” form of security. Behavioral biometrics authenticates you based on your unique human quirks.
The bank’s app, running on your phone, quietly learns you.
- How fast do you type your password?
- What is the rhythm of your keystrokes?
- At what angle do you typically hold your phone?
- How do you swipe your thumb across the screen?
These patterns are as unique as a fingerprint, but impossible for an AI to deepfake.
A scammer might have your password, but they don’t type like you. They don’t hold the phone like you. The moment they log in, the bank’s AI system can see the “behavioral signature” is wrong, flag the session as high-risk, and demand more verification, like a liveness check.
Advanced Fraud Analytics and AI: Fighting Fire with Fire
Banks are using their own AI scam detection models to combat criminal AI. In a Zero Trust model, every transaction is analyzed.
How AI Detects Anomalous Behavior in Real-Time
Your bank’s AI knows your “normal.”
- You always buy groceries on Saturday at 10:00 AM.
- You never send wire transfers to offshore accounts.
- You log in from Chicago 99% of the time.
A Zero Trust system watches for deviations. A login from a new device, followed by a large, unusual wire transfer request to a new recipient, is a massive red flag. The system can automatically freeze the transfer and trigger a mandatory multi-factor authentication for online banking, like sending a code and requiring a liveness check, before the money moves.
What This Means for You: How to Protect Yourself from AI Scams
This new security is fantastic, but it also requires a new level of vigilance from us. You are the first line of defense. Here are practical AI scam prevention tips for bank customers.
How to Spot a Deepfake Voice Call (The “Callback” Method)
If you receive a “panicked” call from a bank or a loved one, even if it sounds exactly like them, your new response must be:
“I’m going to hang up and call you right back on the number I have saved for you.”
A scammer will try to keep you on the line. “No, it’s urgent! Don’t hang up!” A real bank employee or family member will understand. Hang up. Call the bank’s official phone number from their website. Call your loved one’s known number. This single step defeats 99% of all voice phishing scams.
Identifying AI-Powered Phishing Emails
- Check the Sender’s Email: Look closely. Scammers will use “microsquatting.” The real email is
john.doe@bank.com. The fake isjohn.doe@bank-security.comorjohn.doe@bank.co. - Beware of Urgency: “Immediate Action Required,” “Account Suspension Notice.” These are psychological tricks. A real bank will not close your account via a single email.
- Hover, Don’t Click: On a computer, hover your mouse over any link. The preview (usually in the bottom corner of your browser) will show you the real destination. If it looks like
http://bit.ly/secure-portal, it’s a scam.
Securing Your Online Banking: Beyond a Strong Password
- Enable MFA Everywhere: Use an authenticator app (like Google Authenticator or Authy), not just SMS texts. Hackers can (and do) swap your SIM card to steal your text messages.
- Set Up Account Alerts: Turn on all alerts in your banking app. Get a text or push notification for every transaction, login, or password change.
- Never “Verify” Data: A real bank will never call or email you to ask for your password, PIN, or full social security number. They already have it. If someone asks for it, it’s a scam.
The Future of Bank Security: Zero Trust and Beyond
This is an arms race. As banks deploy liveness detection, scammers will build AI that can pass it. So, is Zero Trust the permanent solution for AI fraud?
Yes and no. Zero Trust is a philosophy of continuous adaptation. It’s not a “set it and forget it” solution.
The Challenges of Implementing Zero Trust in Legacy Banking Systems
One of the biggest hurdles for banks is their old technology. Many large banks still run on “mainframe” systems built in the 1970s and 80s. You can’t just “install” Zero Trust on these systems.
This is why implementing a zero trust framework is a slow, expensive, and difficult process. They have to painstakingly add new layers of identity management and microsegmentation on top of (or around) these ancient systems without breaking them.
The Future of Identity: Decentralized Identity
The next step beyond Zero Trust may be to take your identity away from the bank entirely. With decentralized identity or “verifiable credentials,” you would hold your own identity on your phone in a secure, cryptographic wallet.
When a bank needs to verify you, your “identity wallet” would just send them a cryptographic proof that says “Yes, this person is over 18” or “Yes, this person’s name is John Smith,” without ever sending your actual driver’s license or social security number. This makes a data breach at one company useless.
This, combined with the benefits of a Zero Trust Network Access (ZTNA) model, creates a future where security is personalized, verifiable, and not dependent on a single password.
Final Thoughts: Security is a Process, Not a Product
The war against financial fraud has entered a new, intelligent era. AI has armed the attackers with weapons of perfect impersonation.
In response, the financial world has been forced to adopt a new, hardened mindset: trust nothing, check everything. The Zero Trust security model is not just a buzzword; it’s the single most important security shift of our generation. It’s the digital equivalent of moving from a single castle wall to a high-tech fortress with biometric checkpoints, internal blast doors, and behavioral scanners in every hallway.
For you, this means your banking experience will become more secure, but it might also involve more “friction”—more login steps, more identity checks, more “liveness” videos.
Do not be annoyed by this. Be thankful. Every extra step is another wall between a scammer and your life savings. In this new world, the only safe path forward is one of vigilance, skepticism, and the fundamental belief that trust must be earned, not given.
Frequently Asked Questions About Zero Trust and AI Scams
1. What is the main difference between Zero Trust and a traditional firewall?
A firewall is a “castle wall” that trusts everyone inside the network. Zero Trust trusts no one, inside or out. It acts like a security checkpoint in every room of the castle, continuously verifying every user and device, even after they are “inside.”
2. Is Zero Trust the same as a VPN?
No. A VPN (Virtual Private Network) is a “secret tunnel” into the trusted network. A Zero Trust Network Access (ZTNA) model is the replacement for a VPN. ZTNA connects a specific user to a specific application (e.g., you to the email server) and nothing else. It never gives you full access to the entire network, which is much more secure.
3. Can AI really detect deepfakes?
Yes, this is an active arms race. Banks and security firms are building AI models (a “fighting fire with fire” approach) that are trained to spot the tiny, invisible flaws in AI-generated content. This includes unnatural blinking, strange lighting, digital “artifacts” in the audio, or “behavioral” signs, like how a user interacts with an app.
4. What is the “least privilege access” principle of Zero Trust?
It’s the simple idea that any user or system should only have the absolute minimum level of access needed to perform its specific task. A bank teller’s computer should only be able to access customer data, not the bank’s HR or network settings. This minimizes the damage an attacker can do if they steal that teller’s credentials.
5. How do I protect myself from an AI voice cloning scam?
Use the “callback method.” If you get an urgent, panicked call from a loved one or your bank asking for money or personal information, hang up. Then, call them back on the official, trusted phone number you have for them. A scammer can’t intercept that call.
6. What is “behavioral biometrics”?
This is a cutting-edge security measure. It’s how your bank’s app identifies you by your unique behaviors—the way you type, the speed of your mouse movements, the angle you hold your phone, or the way you swipe. It’s much harder for a scammer to fake than a password or even a fingerprint.
7. Why are banks making me do “liveness checks” (like blinking or turning my head)?
They are using this to defeat deepfake video and photo attacks. A static photo can’t blink, and a pre-recorded deepfake video can’t respond to a random command in real-time. This proves a live person is in front of the camera.
8. Are deepfake scams a real threat or just media hype?
They are a very real and growing threat. TheFBI’s Internet Crime Complaint Center (IC3)has issued multiple warnings about the use of deepfakes in both corporate (Business Email Compromise) and personal (family emergency) scams, leading to millions of dollars in losses.
9. What is “microsegmentation” and why does it matter?
It’s a key part of Zero Trust. It means breaking a large computer network into thousands of tiny, isolated zones. This prevents an attacker from moving around. If they break into one “room” (like the email server), they are trapped there and can’t get to the “vault” (the customer database).
10. What’s the best way to secure my online bank account right now?
Enable multi-factor authentication (MFA) using an authenticator app, not just SMS/text. An app (like Google Authenticator) is not vulnerable to “SIM-swapping” attacks. This is the single biggest security upgrade you can make.
11. What is “synthetic identity fraud”?
This is an advanced scam where criminals use AI to combine real and fake information (e.g., a stolen social security number, a fake name, a generated address) to create a brand new, “synthetic” person. This fake person then applies for real loans and credit cards.
12. Is Zero Trust 100% foolproof?
No security model is 100% foolproof. However, Zero Trust is designed to minimize the damage and maximize detection time. It assumes a breach will happen. Its goal is to stop that breach from becoming a catastrophe by isolating the threat and verifying everything, all the time.