The digital bells of the stock exchange, the silent hum of an ATM, the instant “approved” on a credit card swipe—these are the heartbeats of the modern economy. But what if they all stopped? This isn’t a scene from a movie. It’s the real-world scenario that keeps bankers, regulators, and cybersecurity experts awake at night. The threat? Ransomware.
For years, we’ve viewed ransomware as a costly IT problem, a digital mugging. But when this threat targets the financial services industry, it transforms. It’s no longer just a “cyber attack”; it becomes a potential ransomware as a systemic financial risk. This is the new bank heist, and the thieves aren’t after the cash in the vault—they’re after the entire system.
Financial institutions are, by an overwhelming margin, the prime targets for these sophisticated attacks. The reasons are obvious, but the consequences are complex and interconnected, threatening to cause a domino effect that could impact the entire global economy.
This in-depth article explores why the financial industry is ground zero for ransomware, how an attack on one bank could trigger a systemic crisis, and the advanced, next-generation defensive tech financial institutions are deploying to build a digital fortress.
The New Bank Heist: Why the Financial Services Industry is Ransomware’s Number One Target
Ransomware gangs operate like multinational corporations. They have R\&D, marketing (Ransomware-as-a-Service, or RaaS), and a laser-focus on maximizing their return on investment (ROI). From their perspective, the financial services industry is the most lucrative target on Earth for several key reasons.
Target 1: The Unmatched Value of Financial Data
Money isn’t just paper; it’s data. Financial institutions are the guardians of the world’s most sensitive and valuable information. Attackers aren’t just encrypting files; they are stealing the data first. This is known as “double extortion.”
- Personally Identifiable Information (PII): Names, addresses, Social Security numbers.
- Nonpublic Personal Information (NPI): Bank account numbers, credit card details, loan applications, investment portfolios, and transaction histories.
This data is incredibly valuable on the dark web. But for the ransomware gang, its value is even higher as leverage. They don’t just say, “Pay us to unlock your files.” They now say, “Pay us, or we will leak all of your customers’ financial data and report you to the regulators.” For a bank built on trust, this is a catastrophic threat.
Target 2: The Crippling Cost of Downtime
What is the impact of ransomware on the banking sector? Consider this: a bank that can’t process transactions is not a bank. The financial industry operates on millisecond-level availability.
- Trading Systems: A trading floor that is down for even an hour can result in billions in losses.
- Payment Networks: If a bank can’t connect to payment rails like SWIFT, Fedwire, or ACH, global commerce can grind to a halt.
- Customer Access: If millions of customers can’t access their online banking or use their debit cards, panic and a loss of confidence will follow.
This critical need for 100% uptime creates immense pressure. Attackers know that every minute a bank is offline, the cost multiplies exponentially. This gives the bank an overwhelming incentive to pay the ransom quickly just to get services back online, even if they have backups.
Target 3: The “Deep Pockets” Perception and Reality
It’s simple logic. Ransomware gangs target entities they believe can afford to pay massive ransoms. Financial institutions, hedge funds, and insurance companies are perceived as having deep pockets. Attackers set their ransom demands accordingly, often demanding tens of millions of dollars—a sum they know their target can technically pay, even if it’s painful.
Target 4: Complex Legacy Systems and a Sprawling Attack Surface
Many established financial institutions are not digital natives. They are often running on a complex patchwork of technology:
- Decades-old mainframe systems running core banking ledgers.
- Modern, customer-facing cloud applications and mobile apps.
- A vast network of third-party vendors and partners, each with its own security.
This hybrid environment is incredibly difficult to secure. A single weak link—an unpatched server, a compromised third-party vendor (a supply chain attack), or one employee falling for a sophisticated phishing email—is all an attacker needs to gain entry.
Beyond a Single Bank: How Ransomware Becomes a Systemic Financial Risk
This is the most critical part of the problem. A ransomware attack on one bank is a terrible event. A coordinated attack on multiple banks, or a successful attack on a critical piece of shared financial infrastructure, is a potential systemic crisis.
Understanding the Contagion Effect in a Connected System
Systemic risk is the risk that the failure of one component in a system will trigger a cascade of failures, bringing down the entire system. Think of it as a domino effect.
The financial system is the most interconnected system in the world. Banks don’t exist in a vacuum. They are constantly moving money between each other, settling trades, and relying on central clearinghouses and payment processors.
Now, imagine a successful ransomware attack on a major payment processor or a central counterparty (CCP) that clears trillions of dollars in trades every day.
- Gridlock: Transactions stop. Banks can’t settle payments with each other.
- Liquidity Freeze: A bank expecting a large payment doesn’t receive it. It can’t, in turn, make its own required payments. This “liquidity freeze” spreads instantly.
- Loss of Confidence: The public and other financial institutions see that the system is broken. Trust evaporates.
This contagion risk from a financial cyber incident is what regulators fear most. It’s not just about one company’s data; it’s about the fundamental trust and operability of the entire market.
The Nightmare Scenario: A “Run” on the Digital Bank
We all know what a traditional bank run looks like from old movies: people lining up outside a bank branch to pull out their cash.
A digital bank run caused by ransomware would be infinitely faster and more chaotic.
- An attack locks a bank’s systems.
- Customers can’t access their online accounts or use ATMs.
- News and social media spread rumors that the bank is insolvent or “hacked.”
- Customers of other banks, fearing the contagion, frantically try to pull their money out, overwhelming other institutions.
In this scenario, the loss of confidence becomes a self-fulfilling prophecy, creating a liquidity crisis that could topple even healthy banks. This is how ransomware evolves from an IT problem to a full-blown financial stability threat.
The Evolution of the Threat: From Double to Triple Extortion
Ransomware groups are not static; they innovate.
- Double Extortion: They encrypt your files (extortion 1) AND steal your data, threatening to leak it (extortion 2). This beats the “we have backups” defense.
- Triple Extortion: They do both of the above AND launch a Distributed Denial-of-Service (DDoS) attack to knock the bank offline (extortion 3). Or, they might contact the bank’s customers, regulators, and the media directly, maximizing the reputational damage.
For a financial institution, this is a multi-front war. They are fighting to restore systems, prevent a catastrophic data breach, and manage a public relations and regulatory crisis all at once.
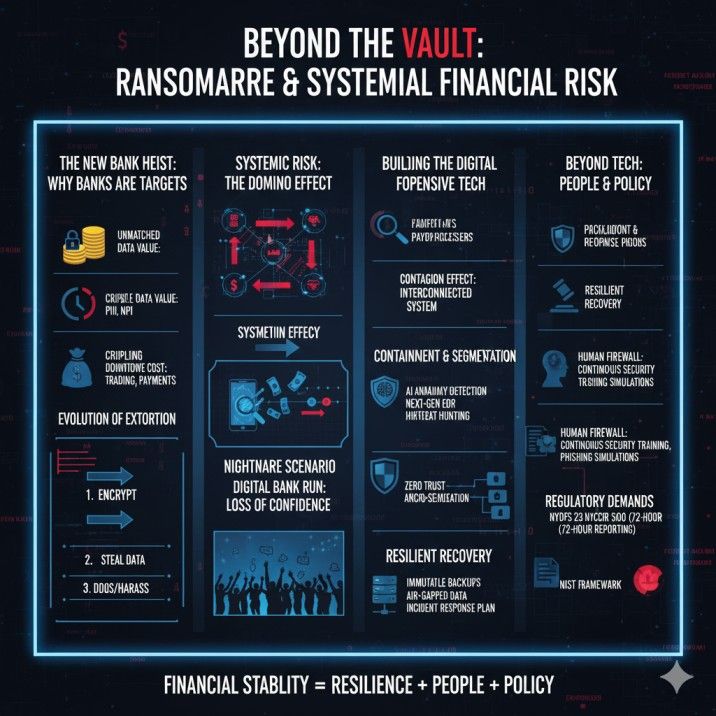
Building the Digital Fortress: Defensive Tech Banks Use to Combat Ransomware
Because the stakes are so high, the financial services industry is pouring billions of dollars into a multi-layered defense. They operate on the assumption that a breach is not a matter of “if” but “when.” The goal is resilience—the ability to take a punch and keep functioning.
Here is the advanced defensive tech being deployed by financial institutions today.
Pillar 1: Advanced Prevention and Detection
You can’t just block “known” viruses anymore. Modern attacks are more subtle.
- AI and Machine Learning for Anomaly Detection: Banks use sophisticated AI models to learn the “normal” behavior of their network. The AI establishes a baseline for every user, server, and application. When it spots a deviation—like a user’s credentials suddenly trying to access thousands of files at 3 AM from a different country, or a server suddenly trying to encrypt data—it triggers an alert and can automatically lock the account before the ransomware detonates.
- Next-Generation Endpoint Detection and Response (EDR): Think of this as antivirus on steroids. Traditional antivirus looks for known “signatures” of a virus. EDR, on the other hand, monitors behavior. It watches for the techniques attackers use (e.g., “a Word document just launched a command prompt which is trying to connect to a suspicious IP address”). When it sees this malicious chain of events, it doesn’t just block the file; it can immediately isolate the infected computer from the network, stopping the ransomware from spreading.
- Proactive Threat Hunting: This is a human-led defense. Instead of waiting for an alarm, elite cybersecurity teams within the bank actively “hunt” for intruders in their own network. They search for the subtle clues that an attacker is already inside, performing reconnaissance before launching the main attack.
Pillar 2: Containment and Segmentation Strategies
The most important goal once a breach occurs is to stop the “lateral movement” of the attacker. You want to contain the fire to one room.
- The Zero Trust Architecture (ZTA) Model Explained: The old security model was a “castle and moat”: a strong perimeter, but once you were inside, you were trusted. The Zero Trust model assumes the attacker is already inside. The motto is “Never trust, always verify.” In a Zero Trust environment, every single request—from a user, a device, or an application—must be authenticated and authorized before it can access any data or resource. This makes it incredibly difficult for an attacker to move from one system to another.
- Micro-segmentation in Practice: This is a key part of Zero Trust. Instead of having one big, flat network, banks use micro-segmentation to break the network into thousands of tiny, isolated zones. A server holding loan applications is in its own secure segment, separate from the server holding customer email. If ransomware infects the email server, the segmentation rules act as digital bulkheads, preventing it from ever reaching the critical loan data.
Pillar 3: Resilient Recovery and Response
This is the last line of defense: how to recover when all else fails.
- The Power of Immutable Backups and Air-Gapping: This is perhaps the most critical defense. Ransomware attackers are smart; their first move is often to find and encrypt the backups. To prevent this, banks use:
- Immutable Backups: These are backups that, once written, cannot be altered or deleted by anyone (even an administrator) for a set period. The ransomware simply can’t encrypt them.
- Air-Gapped Backups: This is a physical or logical separation. A true air-gap means the backup data is stored on a system (like tape) that is not physically connected to the network. It’s the digital equivalent of putting your gold in a separate vault that isn’t even on the same map.
- Developing a Comprehensive Ransomware Incident Response Plan: Banks have a detailed playbook for what to do the moment an attack is detected. This plan, which is practiced regularly, outlines who to call, which systems to shut down first, how to communicate with regulators, and the precise steps to restore from immutable backups. You can review a general framework for this from the Cybersecurity and Infrastructure Security Agency (CISA).
- Ransomware Negotiation and Payment: The Great Debate: Does the bank have a plan to pay? Most financial institutions will not admit it, but many retain third-party “ransomware negotiation” firms. While law enforcement, including the FBI, strongly discourages paying ransoms, the bank must weigh that against the systemic risk of being offline. It’s a complex business and ethical dilemma.
Beyond the Tech: The Role of People, Policy, and Regulation
Technology alone is not enough. The defense of the financial system rests on a three-legged stool: technology, people, and policy.
Strengthening the Human Firewall: Continuous Security Training
Over 90% of ransomware attacks start with a human error, most often a phishing email. Banks are moving away from the boring annual “click-through” training. The new standard is continuous security awareness and simulation:
- Regular, sophisticated phishing tests that mimic real-world attacks.
- “Just-in-time” training: If an employee clicks a simulation link, they get an immediate, 2-minute video explaining the red flags they missed.
- Building a “see something, say something” culture where employees are rewarded for reporting suspicious emails, not punished for them.
How Financial Regulations (Like NYDFS 500) Force Stronger Defenses
Because the risk is systemic, regulators are no longer making suggestions; they are making demands. In the U.S., a web of agencies (OCC, FFIEC, FRB) and state-level bodies oversee bank cybersecurity.
The most famous of these is the New York Department of Financial Services (NYDFS) 23 NYCRR 500. This landmark regulation mandates that all financial institutions licensed in New York must:
- Maintain a comprehensive cybersecurity program.
- Appoint a Chief Information Security Officer (CISO).
- Implement specific defensive controls (like encryption and multi-factor authentication).
- Report cybersecurity events (including ransomware attacks) within 72 hours.
These regulations, along with other global frameworks like the NIST Cybersecurity Framework, create a mandatory baseline for security, forcing the entire industry to raise its defenses.
Conclusion: The Continuous Arms Race for Financial Stability
Ransomware is far more than a corporate data breach. It is a clear and present systemic risk to the financial stability on which we all depend. The interconnected nature of our banking, trading, and payment systems means that a successful, targeted attack could have cascading consequences that dwarf the initial ransom demand.
Financial institutions, recognizing their role as critical infrastructure, are in a continuous arms race. They are deploying a layered defense of predictive AI, Zero Trust segmentation, and untouchable immutable backups.
But the war is not won with technology alone. It requires a resilient human firewall and strict regulatory oversight. For the financial services industry, security is no longer just a cost center—it is a fundamental pillar of modern-day survival and public trust.
Frequently Asked Questions (FAQ) About Ransomware and Financial Risk
1. What is ransomware as a systemic financial risk?
Ransomware as a systemic financial risk refers to the possibility that a ransomware attack, or a series of attacks, could destabilize the entire financial system, not just one institution. This could happen if an attack hits a critical payment processor, a central clearinghouse, or enough major banks at once to cause a loss of public confidence and a “digital bank run.”
2. Why are banks and financial institutions prime targets for ransomware?
They are prime targets for three main reasons:
- Data: They hold highly sensitive financial data (NPI) that is valuable for extortion.
- Downtime: They cannot afford to be offline, as they process transactions in real-time. This high-pressure environment makes them more likely to pay a ransom quickly.
- Deep Pockets: Attackers believe they have the money to pay multi-million dollar ransoms.
3. What is the difference between double and triple extortion ransomware?
- Single Extortion: “Pay us to unlock your encrypted files.”
- Double Extortion: “We have also stolen your files. Pay us, or we will leak all your sensitive customer data online.”
- Triple Extortion: “We have encrypted your files, stolen your data, and are now launching a DDoS attack to knock you offline. Pay us to make it all stop.”
4. What is a Zero Trust Architecture and how does it stop ransomware?
A Zero Trust Architecture (ZTA) is a security model that abandons the idea of a “trusted” internal network. It operates on the principle of “never trust, always verify.” Every user and device must be continuously authenticated and authorized to access any resource. This stops ransomware from spreading (lateral movement) because even if an attacker gets in, they are trapped in one small segment and cannot “see” or access other parts of the network.
5. How do immutable backups work as a ransomware defense?
An immutable backup is a backup file that, once created, cannot be changed, encrypted, or deleted for a set period. Even an attacker with full administrator credentials cannot tamper with it. This makes it a “gold copy” for recovery. If a bank is hit with ransomware, they can confidently ignore the ransom demand, wipe the infected systems, and restore their critical data from these untouchable backups.
6. What is the role of AI and machine learning in stopping ransomware?
AI and machine learning are used for behavioral-based threat detection. Instead of looking for known viruses, the AI learns the “normal” pattern of activity on the network. It can then spot anomalies that signal an attack in progress—like a user account suddenly encrypting files at high speed. The AI can then automatically block the activity and isolate the user before the full attack can succeed.
7. What is EDR (Endpoint Detection and Response)?
EDR is an advanced cybersecurity solution that monitors all “endpoints” (laptops, servers, mobile phones). It provides real-time visibility into an endpoint’s activity and can detect malicious behaviors (like those used by ransomware) that traditional antivirus software would miss. When a threat is detected, EDR tools can automatically contain the threat by isolating the device from the network.
8. What is micro-segmentation?
Micro-segmentation is a security technique that divides a data center or cloud network into small, logically-isolated zones. This creates “digital bulkheads” between applications and servers. If ransomware infects one segment, it is prevented from spreading to any other part of the network, containing the damage to a very small area.
9. Should financial firms pay the ransom?
This is a highly controversial topic. Law enforcement (like the FBI) strongly advises against paying ransoms because it funds criminal organizations and encourages more attacks. However, a financial institution must weigh this against the potential catastrophic cost of downtime and the risk of systemic contagion. Many firms hire professional negotiators to manage the situation, but the official public stance is almost always “do not pay.”
10. What is a “digital bank run”?
A digital bank run is the modern equivalent of a traditional bank run. It’s a crisis of confidence where a large number of a bank’s customers try to withdraw their funds simultaneously over online and mobile platforms. This could be triggered by a ransomware attack that either takes the bank offline or leads to rumors of insolvency, causing panic.
11. How does a ransomware incident response plan work for a financial institution?
An incident response (IR) plan is a detailed playbook. It typically includes:
- Detection: How to identify the attack.
- Containment: The first priority is to stop the spread (e.g., “unplug” affected systems, trigger micro-segmentation).
- Investigation: Using forensics to determine how the attackers got in and what they touched.
- Eradication: Removing the ransomware from all systems.
- Recovery: Restoring data from immutable backups.
- Communication: Notifying executives, legal teams, regulators (often within a 72-hour window), and customers.
12. What is NYDFS 23 NYCRR 500?
It is a cybersecurity regulation from the New York Department of Financial Services. It is considered one of the strictest in the world and applies to any financial company licensed to operate in New York. It mandates specific technical controls (like encryption), requires companies to have a CISO, and sets a 72-hour deadline for reporting breaches.
13. What is the impact of a ransomware attack on a bank’s customers?
The immediate impact is the loss of access to services—online banking, ATMs, and even card payments may not work. The long-term impact is the risk of data theft. If the bank’s data is leaked, customers’ personal and financial information could be sold and used for identity theft and fraud for years to come.
14. How does the “human firewall” prevent ransomware?
The “human firewall” refers to the collective vigilance of a company’s employees. Since most ransomware attacks start with a phishing email, a well-trained workforce that can identify and report suspicious emails is the best first line of defense. They act as a security sensor, preventing the attack from ever succeeding.
15. What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a criminal business model. A core group of developers creates the ransomware “product” and then licenses it to “affiliates.” These affiliates carry out the attacks and pay the developers a percentage of the ransom. This model has lowered the bar for entry, allowing less-skilled criminals to launch highly sophisticated attacks, which has led to the explosion in ransomware incidents.