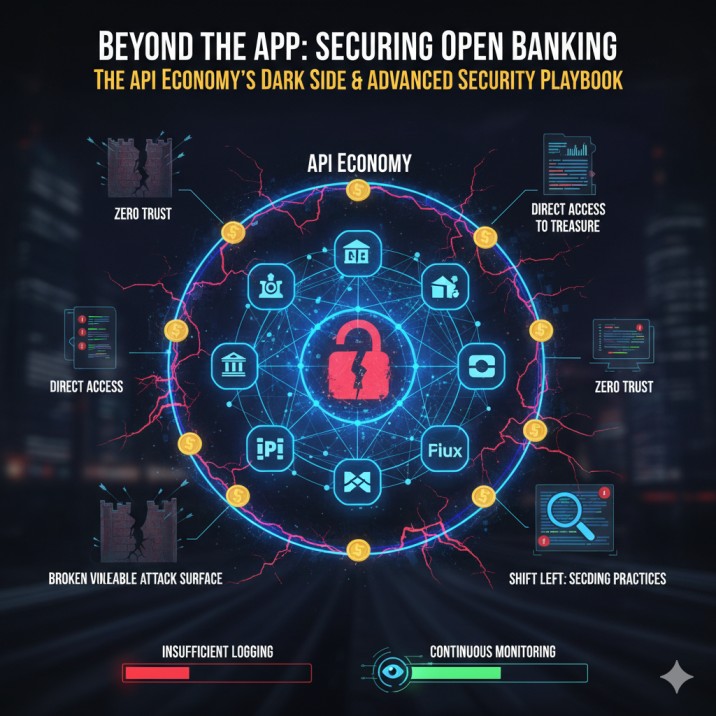
We all love the convenience.
You open a single app on your phone, and in seconds you can see your bank balance, check your investment portfolio, pay a friend, and get a loan offer. This is the magic of the API Economy, an interconnected world where FinTech apps and banks share data seamlessly to create better, faster user experiences. This is the promise of Open Banking.
But there’s a dark side to this magic.
Every single one of those connections, every “API” (Application Programming Interface), is a new, invisible door into the bank’s vault. While we see a slick, simple app, attackers see a sprawling, complex, and new, vulnerable attack surface.
The very “interconnected FinTech apps” that give us convenience have created a security nightmare. The old “castle-and-moat” security model is dead. Today, the attackers are already inside the walls, using the very APIs you built to innovate as their primary weapon.
Securing this new financial ecosystem isn’t just an IT checklist. It’s a battle for survival. This is a deep dive into the API economy’s dark side and the advanced-level playbook you need to secure your financial platforms.
The API-First World: What Is the Attack Surface We’re Defending?
Before we can fight the enemy, we have to understand the battlefield. The API-first financial ecosystem has fundamentally changed the game.
What is the API Economy in FinTech and Open Banking?
Think of an API as a waiter in a restaurant.
You (the user in a FinTech app) don’t go into the kitchen (the bank’s database) to get your food. You give your order (a request for your balance) to the waiter (the API). The waiter goes to the kitchen, gets the specific dish you asked for, and brings it back to you.
Open Banking is a set of rules and technologies that standardizes this “waiter” service across all banks. It forces them to build secure APIs so you can give permission to a trusted FinTech app (like a budgeting tool) to call that waiter on your behalf.
This has led to an explosion of interconnected FinTech apps and new business models like:
- Embedded Finance: Getting a loan directly on an e-commerce site.
- Banking as a Service (BaaS): A non-bank company (like a retail brand) using APIs to offer its own branded bank accounts.
The New, Vulnerable Attack Surface: Why Financial APIs are a Goldmine
This all sounds great for innovation, but for a hacker, it’s a dream come true. Here’s why FinTech APIs are a prime target for attackers.
- Direct Access to Treasure: Financial APIs are a direct pipe to the most valuable data on earth: Personally Identifiable Information (PII), bank account numbers, transaction histories, and credentials.
- Systemic Weakness: An API is a computer talking to a computer. It’s built for speed and efficiency, and security is often an afterthought. Attackers can automate millions of attacks per hour, probing for a single flaw.
- A Web of Third-Party Risk: Your FinTech app might be secure, but what about the 10 different third-party APIs it connects to? One for credit checks, one for KYC (Know Your Customer), one for payments, one for stock data. A breach in any one of these partners can create a supply chain attack that compromises your data. This is the core of managing third-party API risks in open banking.
The scariest part? Many companies don’t even know all the APIs they have. “Shadow APIs” (built by developers for a “quick fix” and forgotten) and “Zombie APIs” (old, unmaintained versions) are left open, unmonitored, and waiting to be exploited.
The Rogues’ Gallery: Top API Security Vulnerabilities Plaguing Open Banking
To defend against attacks, you need to think like an attacker. The most important resource for this is the OWASP Top 10 API Security list. This isn’t a theoretical list; it’s a “most wanted” list of the exact flaws hackers are exploiting right now.
Let’s look at the most critical ones for FinTech.
The King of All Flaws: OWASP API1 – Broken Object Level Authorization (BOLA)
If you learn only one API vulnerability, this is it. BOLA is the biggest security risk in Open Banking, and it’s shockingly simple.
- What it is: BOLA is when an API endpoint lets you see or change data that isn’t yours, simply by changing an ID number.
- The FinTech Attack:
- A user logs into their banking app and requests their transactions. The app calls the API:
https://api.bank.com/v1/users/12345/transactions - The attacker, who is also a user, sees this request. They simply change the ID in their own request:
https://api.bank.com/v1/users/12346/transactions - If the server only checks if the attacker is a valid user (which they are) but fails to check if they are the owner of account
12346, the API returns someone else’s entire transaction history.
- A user logs into their banking app and requests their transactions. The app calls the API:
This single flaw has been responsible for massive data breaches. Preventing Broken Object Level Authorization (BOLA) in fintech must be your number one priority. It requires checking ownership on every single request.
OWASP API2: Broken Authentication
This is the classic “weak lock on the front door.”
- What it is: Flaws in how the API checks who you are. This includes insecure API key management, weak passwords, not revoking access for old keys, and authentication bypass.
- The FinTech Attack:
- A developer hard-codes an API key (a long-term password for a program) directly into a mobile app. An attacker “decompiles” the app, steals the key, and now has permanent, trusted access to the bank’s API.
- An API doesn’t require authentication for a “password reset” endpoint, allowing an attacker to change any user’s password.
- A system that doesn’t properly enforce brute-force attack prevention, allowing a bot to try millions of password combinations.
OWASP API5: Broken Function Level Authorization (BFLA)
This is the “regular user, admin power” flaw.
- What it is: The API has different types of users (like “user” and “admin”) but fails to check which type is making the request for a specific function.
- The FinTech Attack:
- A normal user has an API endpoint to view their profile:
POST /api/v1/user/get_profile - An admin user has an API endpoint to create a new admin:
POST /api/v1/admin/create_admin - An attacker, logged in as a normal user, simply guesses the admin endpoint’s path and tries to call it.
- If the server doesn’t check their “role,” the attacker can successfully promote their own account to an administrator, giving them full control.
- A normal user has an API endpoint to view their profile:
OWASP API4: Unrestricted Resource Consumption
This is how an attacker can kill your service (and your budget) without ever stealing a single piece of data.
- What it is: The API doesn’t set limits on the resources (like CPU, memory, or data) a user can request. This leads to API Denial of Service (DoS) in finance.
- The FinTech Attack:
- An attacker finds an API endpoint that lets them request transaction history by date:
/api/v1/transactions?start_date=...&end_date=... - The attacker sets the
end_dateto the year 2070, requesting 50 years of data. This forces the server to run a massive, complex database query. - The attacker then runs this request 10,000 times at once, completely overwhelming the database and crashing the bank’s entire system for all legitimate users.
- This also includes a lack of API rate limiting and throttling, allowing a single user to make millions of calls and rack up huge cloud computing bills.
- An attacker finds an API endpoint that lets them request transaction history by date:
OWASP API7: Server Side Request Forgery (SSRF)
This is one of the most clever and dangerous attacks.
- What it is: An attacker tricks the bank’s own server into making a request on its behalf to a system it’s supposed to trust.
- The FinTech Attack:
- A FinTech app has a feature to “link another bank account.” It asks for the other bank’s logo and provides a field to enter the logo’s URL.
- The bank’s server takes this URL and “fetches” the image to display it.
- An attacker, instead of a URL to a JPEG, provides an internal IP address for the bank’s own network:
http://10.0.0.5/admin-panel - The bank’s server, thinking it’s just fetching a logo, makes a request to its own internal admin panel. Since the request is coming from inside the “trusted” network, it’s allowed, and the attacker gets the data. This is how SSRF creates a backdoor in financial networks.
OWASP API8: Security Misconfiguration
This is the “unlocked door” and “keys under the mat.”
- What it is: All the simple mistakes. Default passwords on a database, verbose error messages that reveal system information (“Error: Cannot connect to database
prod_db_v1on10.0.0.8“), or leaving a “debug mode” on in a live production environment. - The FinTech Attack: An attacker sends a bad request. The server returns a detailed error message that includes the exact software version of the server. The attacker then looks up known vulnerabilities for that specific version and launches a successful, targeted attack.
OWASP API10: Insufficient Logging & Monitoring
This is the vulnerability that makes all other attacks possible.
- What it is: You get hacked, and you don’t even know it. Your system doesn’t log failed login attempts, authorization errors, or sudden spikes in data requests.
- The FinTech Attack: An attacker spends weeks slowly probing your APIs, trying BOLA attacks on every account, one by one. They are generating thousands of “access denied” errors. But because no one is monitoring API security logs, no alarms are raised. The attacker works until they find a single flaw. By the time the data is for sale on the dark web, the breach is months old, and the logs (if they ever existed) are long gone.
The Fortress: A Modern Defense Strategy for Securing FinTech APIs
The threat landscape is scary. But the “dark side” is manageable. Securing your Open Banking platform requires a modern, layered, “defense-in-depth” strategy.
Beyond the Firewall: Implementing a Zero Trust for API Security
The single most important shift you must make is to adopt a Zero Trust security model.
The old model was “castle and moat”: a strong perimeter (firewall) to keep bad guys out. Once you were “in,” you were trusted. This model is useless when your APIs are designed to be public.
Zero Trust has one simple rule: Never trust, always verify.
This means every single API call—even one that seems to come from a “trusted” internal service—must be treated as hostile until it proves otherwise. It must be:
- Authenticated: Who are you? (Prove it.)
- Authorized: Are you allowed to do what you’re asking? (Check the role.)
- Inspected: Is your request safe, or does it look like an attack?
Adopting this mindset is the foundation for all other security. For a deep, technical dive, the NIST Zero Trust Architecture framework is the industry gold standard. You can learn more at the NIST website.
Your API Security Checklist: Practical Steps to Lock Down Attack Surfaces
Here is a practical, advanced-level checklist for how to secure open banking APIs.
Step 1: Discover and Inventory ALL Your APIs
You cannot protect what you do not know exists.
- Action: Use an API discovery and inventory management tool. These tools scan your networks and cloud environments to find all API endpoints, including the shadow APIs your developers forgot about and the zombie APIs from old versions.
- Why it’s advanced: This isn’t just a spreadsheet. A good tool will also classify APIs by risk. Does it handle PII? Does it move money? This “data classification” tells you where to focus your defenses first.
Step 2: Implement Robust Authentication and Authorization
This is your new, intelligent front door.
- Action: Stop using simple, static API keys. Implement the Financial-grade API (FAPI) standard. This is a high-security profile of OAuth 2.0 and OIDC (OpenID Connect).
- Why it’s advanced:
- OAuth 2.0: This is a “valet key.” It lets a user grant a FinTech app limited, short-term permission (e.g., “view balance”) without giving it their actual username and password.
- mTLS (Mutual TLS): This is critical. Normal HTTPS (TLS) only proves the server is legitimate. mTLS for fintech APIs requires both the client (the FinTech app) and the server (the bank) to prove their identities to each other using digital certificates before any data is sent.
Step 3: Layer Your Defenses: WAF, API Gateways, and API Security Platforms
There is no single “silver bullet” product. You need layers.
- Action 1: Use an API Gateway. An API gateway for financial services is a mandatory control point. It’s a “gatekeeper” that sits in front of all your APIs. It’s the only way in.
- Action 2: Enforce Rate Limiting. Your API gateway should be configured for API rate limiting and throttling to stop the DoS attacks we discussed (OWASP API4).
- Action 3: Use a Web Application Firewall (WAF). A modern WAF for APIs can block common attacks before they even reach your code, like SQL injection and cross-site scripting.
- Why it’s advanced: The key is to use a dedicated API security platform that sits behind the gateway. This platform analyzes the behavior of API traffic, using AI and machine learning to find complex BOLA or BFLA attacks that a simple WAF or gateway would miss.
Step 4: Shift Left: Secure Coding Practices for Financial APIs
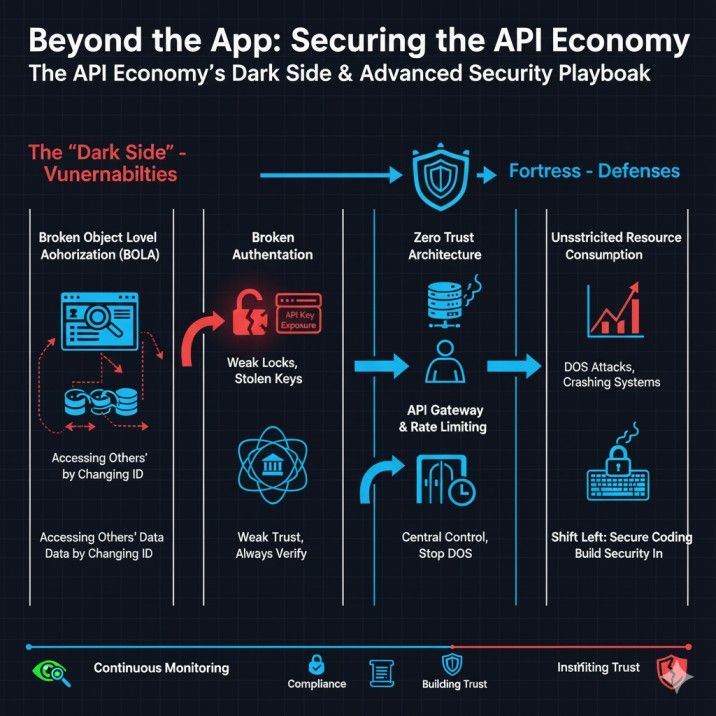
“Shifting left” means building security in from the very beginning (the “left” side of the development pipeline), not trying to “bolt it on” at the end.
- Action: Integrate API security into the CI/CD pipeline. This means every time a developer tries to push new code, it is automatically scanned for security flaws.
- Why it’s advanced: This involves DAST (Dynamic Application Security Testing) for APIs. This tool will automatically run in the development pipeline, attacking the new API code just like a hacker would (testing for BOLA, BFLA, etc.) and failing the build if a vulnerability is found. This “secure coding practice” is far cheaper than fixing a breach in production.
Step 5: Test, Test, and Test Again
The attackers are testing your APIs every day. You should, too.
- Action: You must have a continuous penetration testing for open banking APIs program. This is where you hire ethical hackers (or use an internal “red team”) to try and break your APIs.
- Why it’s advanced: This isn’t just a “once-a-year” test. This should be a “bug bounty” program or a continuous “Red Team as a Service” to find flaws before the bad guys do.
Step 6: Continuous API Monitoring and Logging
This is how you defeat OWASP API10.
- Action: Log everything. Every request, every error, every authorization failure.
- Why it’s advanced: Don’t just log it—monitor it. Feed these logs into a SIEM (Security Information and Event Management) tool. Set up alerts. If a single IP address generates 1,000 “authorization failed” errors in 10 minutes, that’s not a user who forgot their password. That is an active BOLA attack, and your team should be alerted instantly.
The Human and Regulatory Element: Trust and Compliance
Technology is only half the battle. The other half is about trust and rules.
Compliance is Not Security (But It Helps)
The financial industry is (rightfully) swamped with regulations.
- PSD2 (Payment Services Directive 2): This is the European regulation that created Open Banking. Understanding PSD2 API security requirements is non-negotiable.
- GDPR (General Data Protection Regulation): How GDPR and API data breaches intersect is simple: if your API leaks PII, you are facing massive, company-ending fines.
- CCPA, CDR, etc.: Almost every region has its own data privacy and open banking rules.
Here’s the key: API security compliance for fintech is the minimum baseline, not the end goal. PSD2 tells you what to do (e.g., “use strong customer authentication”), but it doesn’t tell you how to stop a BOLA attack. You must go beyond compliance to be truly secure. For more on European regulations, the European Banking Authority (EBA) is the primary source.
Building Customer Trust with Secure APIs
This is the ultimate business case for API security.
You can spend millions on marketing, but a single data breach will destroy your brand overnight. The reputational damage from a fintech API attack is often worse than the financial cost.
Security is no longer a “cost center.” It is a feature. Building customer trust with secure APIs is a competitive advantage. When customers know you have a rock-solid, secure platform, they will trust you with their money.
Conclusion: From a Vulnerable Surface to a Secure Foundation
The API economy has torn down the old walls of banking, and there’s no going back. The innovation and convenience are too powerful.
But this new, open world has a dark side. The new, vulnerable attack surfaces created by Open Banking and interconnected FinTech apps are real, and they are being exploited right now.
The good news is that these attacks are not magic. They are predictable, understandable, and, most importantly, preventable.
By moving from a “castle-and-moat” model to a Zero Trust architecture, by treating the OWASP API Top 10 as your defense playbook, and by layering your defenses—from discovery to design to deployment—you can turn that vulnerable surface into a secure foundation.
In the new API-first world, security is not a feature. It’s the entire platform.
Frequently Asked Questions About API Security in Open Banking
1. What is the biggest security risk in Open Banking?
- By far, the biggest risk is Broken Object Level Authorization (BOLA), also known as OWASP API1. This is a flaw where an API fails to check if the user making a request owns the data they are asking for, allowing attackers to access other users’ accounts just by changing an ID number.
2. What is the difference between Open Banking and BaaS (Banking as a Service)?
- Open Banking is a regulatory framework (like PSD2 in Europe) that forces banks to create secure APIs so customers can share their data with other regulated third-party apps.
- BaaS (Banking as a Service) is a business model where a bank uses its APIs to “rent” its banking license and infrastructure to a non-bank company (e.g., a retail brand) so it can offer its own branded financial products.
3. What is an API Gateway, and why is it important for security?
- An API Gateway is a management tool that acts as a single “front door” for all API requests. For security, it’s critical because it enforces central policies like authentication (who are you?), rate limiting (to stop DoS attacks), and logging (to see who did what).
4. How do I stop BOLA (Broken Object Level Authorization) attacks?
- The only reliable way is to check for ownership on every single request. Your code must have a function that, for every API call that accesses a resource, checks that the authenticated user’s ID matches the owner ID of the resource they are trying to access.
5. What is mTLS (Mutual TLS) and why do fintechs need it?
- Standard TLS (HTTPS) only proves the server’s identity to the client. Mutual TLS (mTLS) is a much more secure standard where both the client and the server must present valid, trusted certificates to prove their identities to each other before any connection is established. This is essential for server-to-server communication in fintech.
6. Isn’t a Web Application Firewall (WAF) enough to protect my APIs?
- No. A traditional WAF is good at blocking common web attacks (like SQL injection) but is often “blind” to API business logic flaws. It might block a malformed request, but it will not understand that a valid request (
/api/users/12346) is actually a BOLA attack. You need a dedicated API security tool for that.
7. What is the FAPI (Financial-grade API) standard?
- The FAPI (pronounced “f-ah-pee”) standard is a high-security “profile” or set of rules built on top of the OAuth 2.0 and OIDC frameworks. It’s specifically designed for the high-risk needs of banking and finance, mandating things like mTLS and stronger authentication.
8. What are “Shadow APIs,” and why are they dangerous?
- Shadow APIs are API endpoints that are active in your production environment but are not documented, tracked, or managed by your security teams. They are often created by development teams for testing or internal use and then forgotten. They are dangerous because they are unmonitored and unpatched, making them a perfect, invisible target for hackers.
9. How do I test my APIs for security vulnerabilities?
- You need a multi-layered testing strategy, including:
- DAST (Dynamic Application Security Testing): Automated tools that “attack” your APIs to find flaws.
- SAST (Static Application Security Testing): Tools that scan your source code for potential vulnerabilities.
- Penetration Testing: Hiring human ethical hackers to try and break your APIs.
10. What is API rate limiting?
- API rate limiting is a security control, usually enforced by an API Gateway, that limits how many times a single user or IP address can make an API request in a given period (e.g., “100 requests per minute”). This is the primary defense against API Denial of Service (DoS) and brute-force attacks.
11. Why is “Insufficient Logging & Monitoring” an OWASP Top 10 risk?
- Because if you are not logging and monitoring your APIs, you are blind. You will not see the thousands of failed login attempts that signal a brute-force attack. You will not see the “access denied” errors that signal a BOLA probe. This lack of visibility allows attackers to work undetected for weeks or months.
12. What is the role of AI and Machine Learning in API security?
- Advanced AI and machine learning for API threat detection is now essential. These systems learn the normal behavior of your APIs (e.g., “User A usually calls these 5 endpoints, from this device, and requests 10-20 transactions”). When an attacker takes over that account and starts calling new endpoints or requesting 10,000 transactions, the AI spots this anomaly as a threat, even if the request looks “valid.”
13. What is a “zombie API”?
- A zombie API is an older, unmaintained version of an API (e.g.,
/v1or/v2) that is still running on your servers even after you’ve released/v3. Like shadow APIs, they are often forgotten, unpatched, and a huge security risk.
14. How does API security relate to GDPR and data privacy?
- Directly. Most financial APIs transport PII (Personally Identifiable Information). A data breach from a poorly secured API (like a BOLA attack) is a direct violation of GDPR, leading to massive fines and reputational damage.
15. What is the first step I should take to improve my API security?
- API discovery and inventory. You cannot protect what you don’t know you have. Run a discovery tool to find all your APIs, including shadow and zombie endpoints. Once you have a complete inventory, you can start to prioritize them and apply security controls.